The Internet is full of Malicious Agents
The cybersecurity threats of 2022 continue to come in, and we’ll have even more next year. You may be wondering what are the biggest cybersecurity threats right now, and in this article we’ll cover our top 5 cybersecurity threats you should be aware of.
What are cybersecurity threats?
These hackers are the root cause of new emerging cybersecurity threats we see on the news, much like the log4j exploit found in 2021 that affected millions of devices. While there are several great resources to help protect you from these online threats, new cyber security threats will always emerge as we introduce new technologies to the public.
Cyber security threats are more prevalent than ever before. The threat of a breach is more than just a matter of losing data, it’s about being prepared to protect you and your assets, defend against financial and reputational loss, and cope with the impact of compromising personal information. Not to mention, the inevitable legal battle that will ensue from a corporate data breach.
As the threat of cyberattacks continues to grow, these risks are forcing businesses and individuals to find new ways to protect themselves. In this report, we will examine five of the most significant cyber security threats (using my assortment of favorite South Park and various giphs to visualize these attacks) and how you can secure your business and family.
Types of cybersecurity threats you should be aware of
Cloud Computing Security
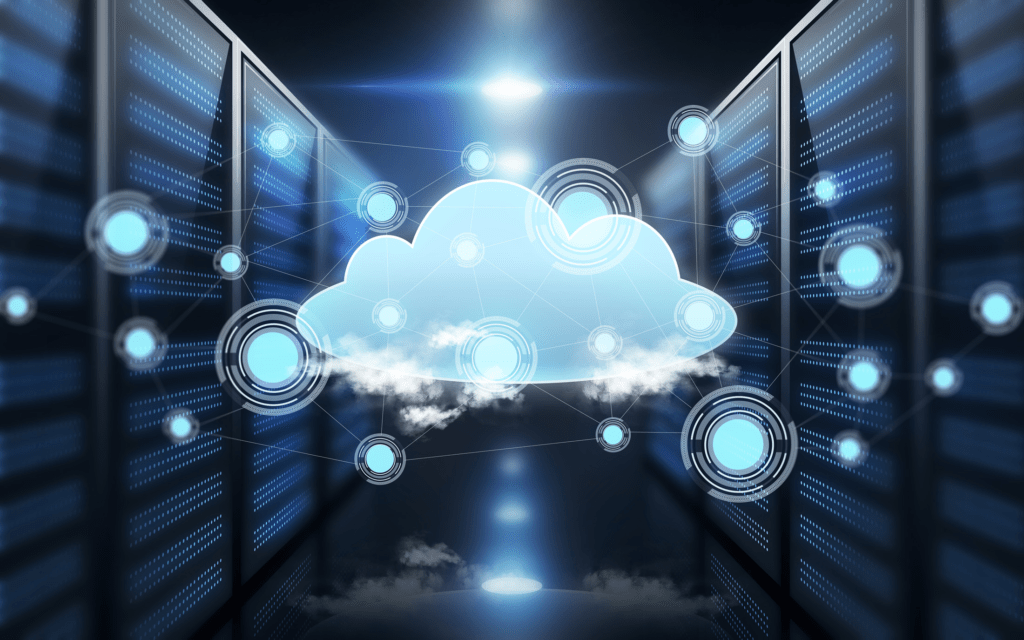
Cloud computing security is likely to be the biggest cybersecurity vulnerability in the future. Cloud computing involves using multiple virtual servers, which may be unattended for long periods of time. This creates a situation where one of the servers can be hijacked and used for malicious purposes. A data breach or stolen information can occur whenever perpetrators gain access to cloud services via a hijacked server or if they are able to hack into a company’s network and steal sensitive data.
Not using cloud computing services will ensure you will not be a victim of a breach in these services. However, it is becoming less feasible to not use cloud computing with major companies making the push to put everything into the cloud.
Some of the good cybersecurity characteristics cloud hosting companies will have include TLS/SSL encryption, encrypting all in-flight data and following good access policies to reduce the number of super users on the system.
Cryptojacking
Ever since the crypto surge of last year, more users are investing in cryptocurrency. Whether you think fortune favors the brave or not, another set of cyber security threats will target digital currency.
Cryptojacking is the act of stealing another’s cryptocurrency assets, whether the attacker targets the coin wallet repository, the wallet holder or the wallets themselves. While you can still use cash for now, this threat becomes a serious issue for folks that have a large amount of capital in cryptocurrency.
The advent of quantum computing is also making brute force attacks more feasible to guess user information. Securing your credentials and only using reputable sources to host your wallet are all ideal. Additionally, moving your wallet offline will increase the difficulty for unauthorized accesses.
Drive-by downloads

The concept of a drive-by download is to quickly get malware onto a computer without the user knowing. This is commonly carried out by users clicking on malicious hyperlinks and visiting bad websites.
Much like a hit and run, these attacks will happen very quickly if you are redirected to a bad link, much like the FoxAcid protocol leaked in the (in)famous Snowden files. Instead of leveraging the faster ISP connection speeds, hackers leverage the refresh rates to make it look like nothing happened.
While this isn’t new compared to the other emerging cybersecurity threats we cover here, it is an important one to be aware of as social engineers are becoming more of a threat.
Social engineering
Social engineering is the art of making someone do whatever you want. In the context of cybersecurity, this means hackers will try to leverage critical situations and/or your lack of knowledge of cybersecurity to convince you they have breached your defenses and will demand you do something so they “won’t leverage it against you”.
In the context of business, individuals will try to leverage your employees or super users to gain access to your resources. Social engineering is nothing new, but it is becoming one of the most common cyber security threats in modern day.
Social engineering attacks are by far the easiest attacks to compose and mass distribute, making these cyber security threats very real for most businesses. Our advice is quite simple: When in doubt, ignore it.
Tracking Software
Giph unrelated… There are several programs out there that have a notorious track record of harvesting user data and selling this information to governments and companies.
As we move into the future, the dependence on these apps will increase and it will be critical to protect your information from these cyber security threats. By limiting the information available online and only posting informative content online will prevent data breaches online.
However, your scrolling habits and content interactions are already being used. Additionally, geolocation, camera and microphones are also favorite targets of these apps on mobile devices. Keeping this in mind, you can disable access in settings when you are not using these features or use a separate device to scroll on.
In Conclusion
The world is becoming increasingly dependent on technology. As this happens, you can expect risks to increase because of hacking, malware, threats from nation states and the rise of artificial intelligence.
Over the next few years, advancements in artificial intelligence and quantum computing will create a storm of new problems and INFOSEC vulnerabilities. Our response as a development company will be to automate incident detection, analysis, containment, and recovery to quickly restore normalcy—all without human intervention.
The nature of cyberattacks is evolving, and hackers are becoming more sophisticated; the next critical infrastructure attack will likely be automated and much harder to detect.
Cyber security threats are always a concern for businesses and individuals. Ensuring businesses follow the best and current cybersecurity standards will help mitigate next generation attacks. By knowing the emerging cybersecurity threats like the ones discussed in this post, you can better prepare for the future cyber landscape.
What are some cyber security threats we missed? Let us know in the comments!

Founder and CEO of R U Coding Me LLC. Jacob obtained his Bachelor’s of Computer Science at the University of Central Florida. He likes to go to the gym and teach people about technology.



